Some of my IR and forensics friends who I highly respect are getting all bent out shape about attribution, or the perceived lack of solid evidence for attribution regarding the DNC attacks. In particular, many of them are now publicly doubting on social media (and mainstream media) that Russia is behind the DNC hacks.
When the Guccifer 2.0 posts came out, these same set of folks analyzed the dump, pretty much everyone in Twitter IR land was convinced the dump was by Russian intelligence services, and Guccifer 2.0 persona a Russian intel persona. Go back, check for yourself, it’s easy to do if you know the usual suspects.
IR and forensics is not my field, so I didn’t really comment at the time, nor really now, except to repeat “attribution is hard, why bother” (particularly relating to attributing to China, which was the previous most common attribution target).
Why bother with attribution?
Because it gets press. Attribution is simply not that useful for the average organisation trying to protect their data … unless they need to take it to court, or you’re a nation state and you want to know who attacked you. Then it becomes vital that it is done properly, and only a few can do this well.
Realistically, my field is protecting information. I find it frustrating when the cyclical fads in our industry lean towards the fatalistic “you’re already hacked, so let’s only detect and respond”, which has been going for nearly three years already, and two years longer than I expected. It must be making money for someone or it seems like security is finally doing a good job, when in fact, we’re only fighting fires, not constructing fire proof artefacts out of flame retardant materials.
If we don’t start work on protecting information BY DEFAULT, we will always be fighting fires, and the world will be on constant fire. That’s crap. We can and should do better than that.
I specialize in helping clients and anyone who consumes my standards work to protect themselves. Building security in costs far less to do the right thing, and this should be the default choice as it’s the most economic investment.
When I help clients protect information, I like to learn how folks in their industrial sector are attacked, so I am very interested in tools, techniques and practices, and to some extent “why” they did it, but I simply don’t need to know who did it. It’s just not relevant.
So I don’t invest in attribution because it is so ridiculously hard to get to a level that would stand up to scrutiny in court. I have colleagues who can do that, but the time and effort taken … well, if your attacker turns out to be a nation state, what are you realistically going to do about it? The same things I am already suggesting you do.
We’re not behind the intelligence kimono
The problem is simple: security agencies with more access than mere mortals don’t share what’s behind the intelligence kimono. Folks outside the kimono either have to trust intelligence agencies on face value, or … you have to state “I don’t personally know, but my opinion is that the evidence is not strong”.
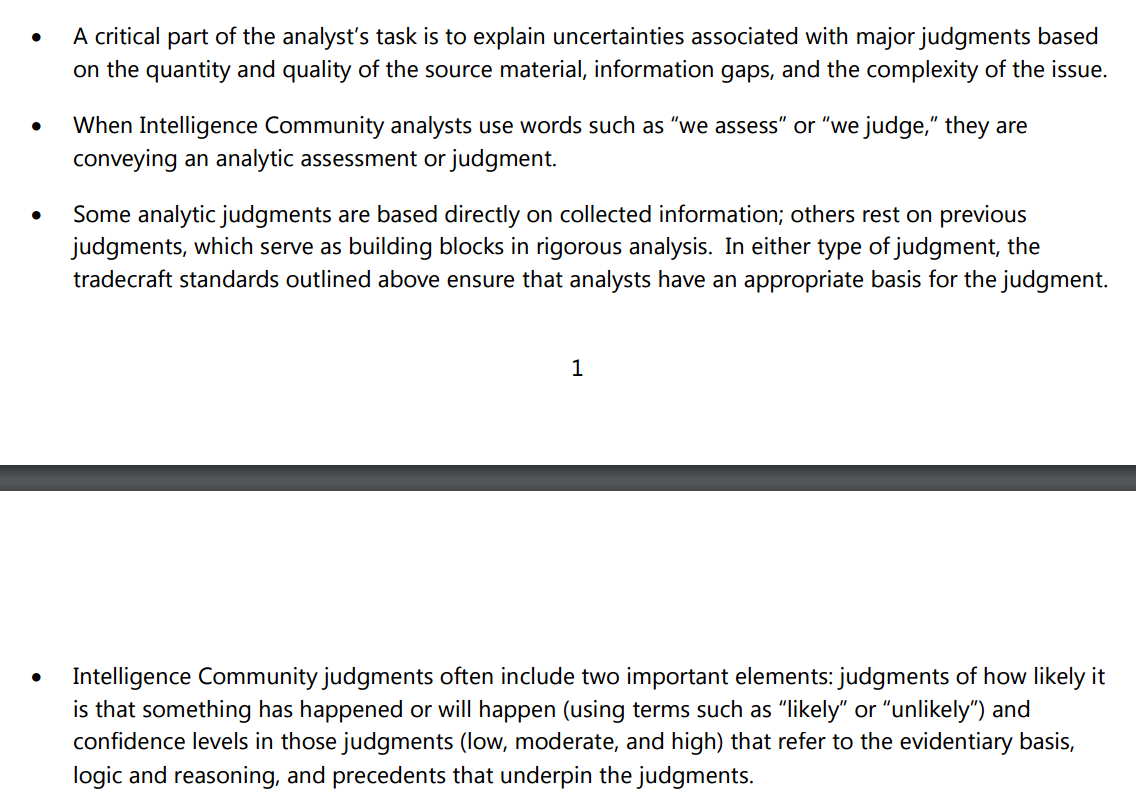
As one of the latest releases says:
It’s perfectly fine and indeed I would expect that my experienced IR and forensic friends to call for a better job of presenting evidence to provide a justification for a particular conclusion without compromising state secrets.
But to state strongly without any more evidence than has been released, such as “It’s country X or Head of State Y” or “There’s no direct evidence, so it’s not Country X or Head of State Y” is at the very least over egging it, and almost certainly wrong. But due to the intelligence kimono, we can’t say for sure.
Intelligence agencies from my understanding rarely state things in black and white terms, but present arguments based around analysis of available (classified) information. Therefore, for the person in the street looking for an easy “It was Country X or Head of State Y”, well, that’s unlikely to ever exist.
What can we take away from this?
Please go easy when making public statements, particularly when we muddy the waters. Understand that there are unknown unknowns, and unless you’re on the inside of the intelligence kimono, those unknown unknowns means we can’t advocate strongly one way or another.
I do hope that intelligence agencies trying to brief the public on classified matters realize that the IT security field contains many awesome subject matter experts, whom will peer review your work for free, either for you, or in the media.
Releasing under-cooked or simply wrong reports is counterproductive. It would be worthwhile to bring in those with a strong IR capability to help create public documents that stand the scrutiny of my dedicated and talented peers.
To my dedicated and talented IR and forensic industry peers, please don’t be “It’s not X” in the media and all over social media. Unless you are inside the intelligence kimono, you have no more information than I do unless someone is blabbing inappropriately. Please work to help government agencies do a better job instead of saying something you can’t prove any more than I can, even with your additional expertise.
In the meantime, let’s not start down the path of distrusting expertise. That way lies failure.

Leave a Reply