In other news, all my talks for OSCON were rejected again. Why did I bother? I should have paid attention my last year’s rant. Most likely, I will have to give up on submitting papers to certain open source developer’s conferences as honestly, why bother doing the work of doing the research, creating the paper and slides only to be rejected? Luckily, two of my submissions were from colleagues, so I didn’t squander a lot of resources on those talks, even though for example, I’m working on porting ESAPI to PHP, which is the subject of one of the rejected talks.
I’ve identified the following security talks for those security folks still considering going to OSCON (although I’d recommend saving your money for OWASP USA as we already have a schedule of 45 web app sec talks in three tracks, and two full days of tutorials, including several two day courses where you’ve got an actual chance of learning something. Just saying.)
- Securing the PHP environment with phpsecinfo, by Ed Finkler. This should be good – I’ve used it before and it’s a pretty cool way to tie down PHP properly. And Ed has contributed Inspekt to OWASP, and therefore he’s cool by me.
- PHP: Architecture, Scalability and Security, by Rasmus. Rasmus knows what he is talking about, but I don’t know how deep the security aspect will be. Hopefully, enough as it’s a three hour talk.
- PHP Taint Tool: It ain’t a parser, by Luke Wellings, a friend of mine from Australia who now lives with his lovely wife in Columbia MD. I’d love to see this tool in action.
- Hack this App! PHP security workshop, the usual sort of scare the punters talk common in talks at conferences I attended about 5-10 years ago. I really hope there’s some solutions in this one. There’s no point in saying you have a problem unless you have a solution, which is what all three of my submitted talks were. Especially the one on securing PHP apps and ESAPI for Java (although we have a completed .NET and soon a PHP port now)
- Perl Security, three hour talk by Paul Fenwick, also an Australian of my acquaintance 🙂
- How to improve quality and security automatically in your open source projects with static analysis, by David Maxwell (Coverity). Hopefully, this is just not a vendor plug, but even if it is … it is about solutions, and I like that.
- Security 2.0: Emerging Trends in Web Application Security, by Chris Shiflett. Also a friend, but sadly, not Australian.
So five talks and two three hour longer talks. Here it is in graphical format for you:
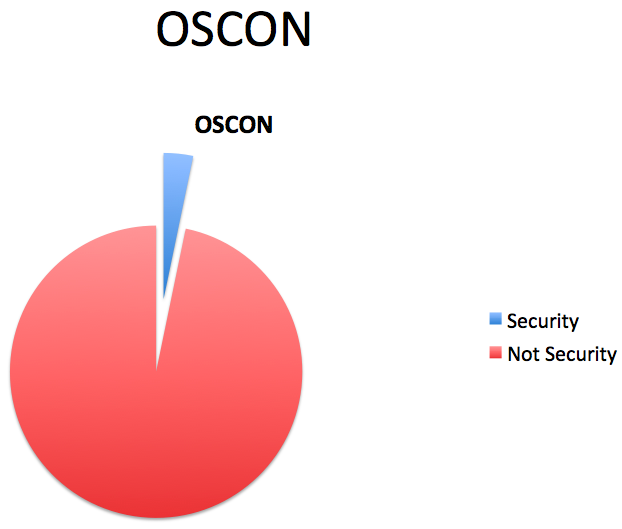
A couple of the talks are likely to not offer that much in the way of solutions. Sadly, no Ruby, Python, administration, database, emerging topics, or people security talks. Worse, there are no Java security talks, which for an semi-incomplete track, I found sort of astounding, especially as I submitted two Java security talks and one PHP talk. The official “security” track has two three hour talks, both detailed above. Even if you look at it from the point of view of OSCON having 16 tracks, hopefully with equal time for all of the tracks assuming there was a lot of competition for speaking slots, there should be 215/16 = ~ 13.4 security talks, not 7.
Although I am glad my friends are accepted whilst talking about security, I think OSCON needs a new program committee. This one is broken.
Leave a Reply